The question what is a VPN arises frequently among professionals, privacy advocates, and IT users alike. In this article, we explain what is a VPN, how it works, the benefits and trade-offs, common types, and real-world applications — delivering clarity to technically literate readers.
What is a VPN exactly?
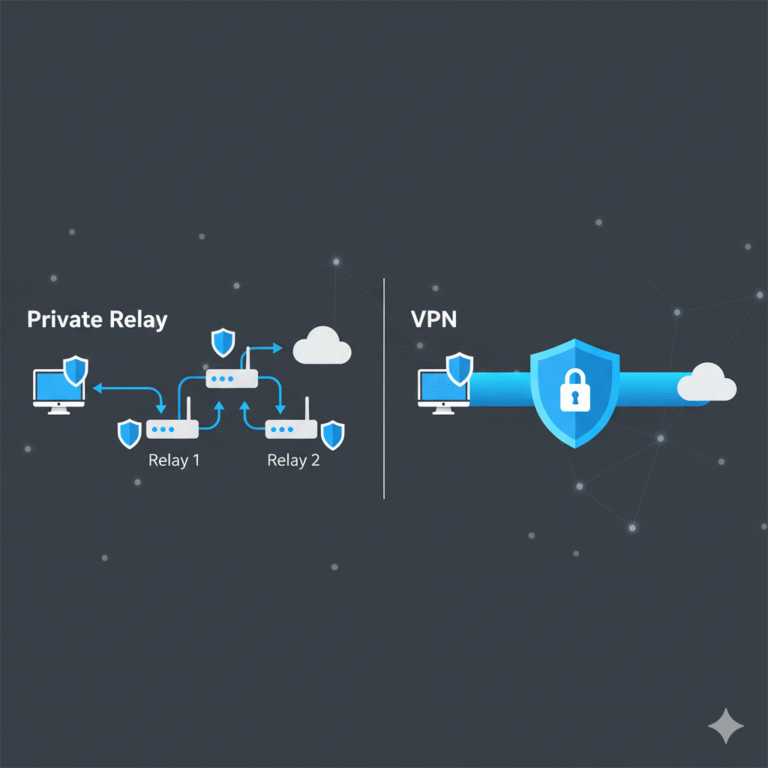
A VPN (Virtual Private Network) is a service or technology that creates an encrypted, private connection between your device and another network over the public Internet. All your traffic is tunneled through that connection, hiding your real IP address and shielding your data from outsiders (source: Cisco) Cisco. In effect, the VPN acts as an intermediary: your device sends encrypted data to the VPN server, and from there the VPN server interacts with external servers on your behalf. This ensures the external servers see the VPN server’s address, not yours (source: CCLA) CCLA.
How does a VPN work?
Encryption & Tunneling
When you enable a VPN, the client application on your device encrypts outgoing data using robust cryptographic algorithms (e.g., AES-256, ChaCha20). That encrypted payload is encapsulated and sent through a tunnel to the VPN server. On the server end, it is decrypted and forwarded to its destination. Responses follow the reverse path, encrypted back to your device (source: EssecurityPlanet) eSecurity Planet.
IP Masking & Routing
While your data is in transit, the VPN server replaces your true IP address with its own, making it appear as if your requests originate from the VPN server’s geographic location. This obfuscation helps maintain anonymity, evade IP-based filters, or access regionally restricted content (source: Fortinet) Fortinet+1.
Protocols & Security
VPNs rely on protocols such as IPsec, OpenVPN, WireGuard, or SSL/TLS. These protocols define how tunnels are established, how encryption keys are exchanged, and how data integrity is verified (source: Palo Alto Networks) Palo Alto Networks+1. Some VPNs also adopt advanced techniques like full-packet encryption to avoid detection in censoring contexts (source: arXiv) arXiv.
Why use a VPN? What are its benefits?
Enhanced privacy and anonymity
A VPN conceals your browsing activity from your Internet Service Provider (ISP), network admins, or public Wi-Fi observers. By encrypting your traffic and masking your IP, a VPN raises the bar for surveillance and tracking (source: Fortinet) Fortinet+1.
Access geo-restricted content
Many streaming services and websites restrict content by country. A VPN enables you to appear in another location and access content that would otherwise be blocked (source: Fortinet) Fortinet.
Secure public Wi-Fi and remote work
Public Wi-Fi is a common attack vector; traffic there is often unencrypted. A VPN protects your connection, making eavesdropping far more difficult. For businesses, VPNs allow remote employees to securely access internal networks (source: Cisco) Cisco.
Network scalability & remote site connectivity
Organizations may use site-to-site VPNs or VPN concentrators to link multiple offices securely over the public Internet. This reduces infrastructure costs while preserving privacy (source: VPN service Wikipedia) For more on this,
what is a vpn concentrator — what is a vpn concentrator: Secure Multi-Tunnel VPN Device.
What are the limitations and trade-offs?
Speed & latency
Encryption and indirect routing introduce overhead. Some slowdown is inevitable, especially if the VPN server is geographically distant or under load (source: Fortinet).
Trust in the VPN provider
Since your VPN provider handles your data in unencrypted form at its endpoint, you must trust that it does not log or misuse your data. Some providers exaggerate “no-logs” claims — always audit their policies and third-party audits (source: Wikipedia, VPN service).
Detection & blocking
Sophisticated networks or governments may block or throttle VPN traffic. In restrictive regions, only VPNs with obfuscation or full-packet encryption may succeed (source: arXiv on evasive VPNs).
Incomplete protection
A VPN does not guard against malware, phishing, browser fingerprinting, or device-level vulnerabilities. Use additional security layers (antivirus, secure browser settings).
When should you use a VPN?
- On untrusted or public Wi-Fi (cafés, airports)
- When accessing region-restricted services abroad
- To protect against network surveillance (e.g. ISP)
- For remote employees to connect securely to internal networks (corporate VPN)
- To mask location-based restrictions or censorship
Not every use case demands a VPN; for day-to-day local web browsing under trusted networks, the performance trade-off may not justify constant use.
Constraints and performance:
- Technical constraints: Testing often occurs from controlled environments; real-world performance may differ due to ISP, routing, server load.
- Performance caveats: Latency and throughput depend heavily on physical distance to VPN server, protocol efficiency, and server infrastructure.
- Guidance: Benchmark with and without VPN, choose nearest and reputable servers, and avoid overloading consumer links. Understand what aspects of performance you’re willing to sacrifice for increased privacy.
What are the main types of VPN?
Remote Access VPN
This is the most common consumer type, connecting an individual device to a remote network through a secure tunnel. It’s used by employees or private users who need encrypted connections to the Internet or a corporate intranet. Popular providers include NordVPN and ExpressVPN — for in-depth evaluations, NordVPN Review — NordVPN Review: Top Features & Performance in 2025 and ExpressVPN Review — ExpressVPN Review – Tested in 2025: Speed, Privacy & Ease.
Site-to-Site VPN
Often used by organizations, a site-to-site VPN connects two or more LANs across different physical sites. For instance, a company with offices in London and New York can share internal resources securely as though both were on the same network. Learn more in which statement describes an important characteristic of a site-to-site vpn — which statement describes an important characteristic of a site-to-site vpn.
Point-to-Point VPN
A subset of site-to-site models, this type creates a direct connection between two network points. It’s simpler to configure and offers strong control over endpoints. See also a point to point vpn is also known as a — a point to point vpn is also known as a site-to-site VPN.
Mobile VPN
Designed for mobile devices that frequently switch networks (e.g., Wi-Fi to 4G), mobile VPNs maintain persistent tunnels through connection changes. This model is crucial for logistics, emergency services, and mobile workforce deployments.
Cloud VPN
Cloud-based solutions operate on infrastructure-as-a-service (IaaS) platforms. They support scalability and hybrid network access, often with identity-based authentication. As cloud adoption grows, these VPNs integrate with SD-WAN and zero-trust frameworks.
How does a VPN differ from similar technologies?
While VPNs encrypt data and mask IPs, they’re not identical to proxies or encrypted DNS systems.
- Proxies route traffic without encryption — useful for anonymity but not privacy. See is ascaler vpn also a proxy server — is ascaler vpn also a proxy server – Clear Insight.
- Encrypted DNS protects DNS queries only, not full traffic. Compare in is encrypted dns an alternative to vpn — Is Encrypted DNS an Alternative to VPN.
- DNSCrypt and similar protocols partially overlap with VPN functions but lack network-wide encryption. For an analytical comparison, refer to is dnscrypt an alternative to vpn — Is DNSCrypt an Alternative to VPN? Explained Simply.
How do VPNs affect gaming and streaming?
For gamers, a VPN can lower or increase ping depending on routing efficiency. Some ISPs throttle gaming traffic, so routing through a VPN may improve consistency — see does using a vpn help with ping — Does Using a VPN Help with Ping? Find Out Now. For streaming, VPNs unlock regional libraries (e.g., Netflix, Disney+), though some services block VPN IPs actively.
If you’re streaming on platforms like JioCinema or TikTok, location spoofing through VPN is straightforward. Read more in how to watch jio cinema in usa without vpn — how to watch jio cinema in usa without vpn – Easy Guide and how to change tiktok region with vpn — How to Change TikTok Region with VPN – Easy Step-by-Step.
Are VPNs legal everywhere?
Legality depends on jurisdiction. In most Western countries, VPNs are legal but regulated. Some regions, such as China, restrict VPN use to government-approved providers. For compliance details, see is vpn legal in china — is vpn legal in china – What You Must Know (2025). Always verify local laws before connecting through offshore servers.
What should you look for in a VPN service?
Encryption standards
Ensure support for AES-256, ChaCha20, or equivalent. Avoid obsolete ciphers like PPTP or outdated L2TP without IPsec.
Logging policy
Choose verified “no-logs” services that publish independent audits. Check transparency reports and data-handling disclosures.
Server distribution
Global coverage enhances access to regional content and redundancy.
Performance and reliability
Look for providers with high-speed backbone networks and native WireGuard support for better throughput. Testing latency with your own connection is essential; see comparative evaluations like AirVPN vs NordVPN — AirVPN vs NordVPN: Which VPN Offers Better Security & Speed?.
What are advanced use cases for VPNs?
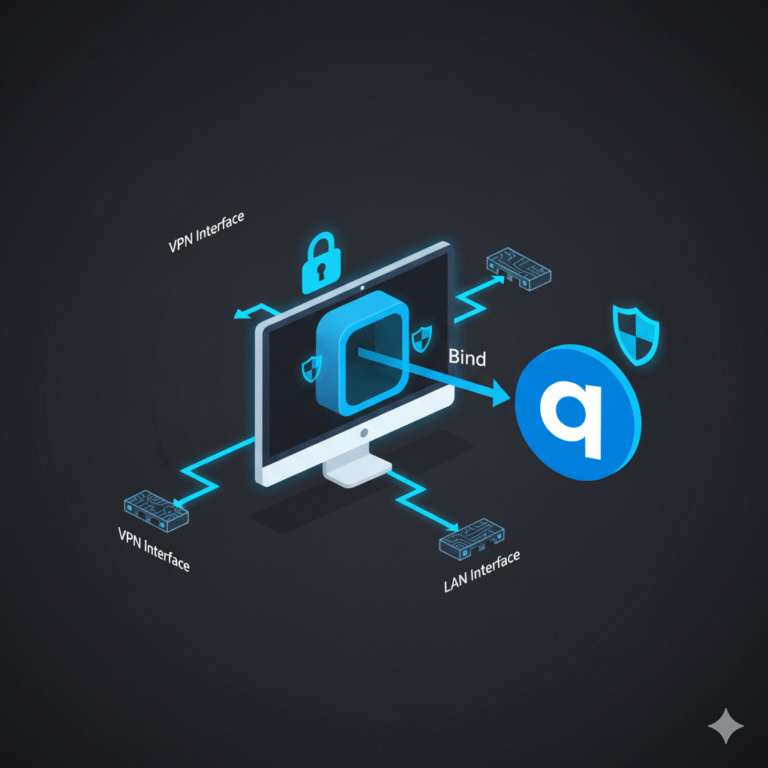
- Torrenting securely: Prevent IP exposure while downloading. Learn configuration steps in how to bind qbittorrent to vpn — how to bind qbittorrent to vpn for secure torrenting.
- Bypassing IP bans: Many platforms enforce IP-based suspensions; VPNs can reassign IPs, though misuse risks account penalties. For details, see can a vpn bypass an ip ban — Can a VPN Bypass an IP Ban? Find Out Now.
- Privacy on shared networks: For home routers and mesh setups, VPN integration secures all connected devices automatically.
Conclusion
Understanding what is a VPN is fundamental for modern cybersecurity and privacy management. From protecting personal data on open networks to ensuring remote workforce connectivity, VPNs deliver versatile security benefits — but only when implemented responsibly. Choosing the right VPN provider, protocol, and configuration ensures you gain both performance and protection in equal measure.
FAQ
Is a VPN 100% safe?
No, a VPN isn’t 100% foolproof. It encrypts your traffic and hides your IP address, but it can’t protect against malware, phishing, or unsafe websites. Always combine VPN use with antivirus software and cautious browsing.
Can a VPN increase Internet speed?
Sometimes. If your Internet Service Provider throttles specific types of traffic (like streaming or gaming), a VPN can bypass throttling and slightly improve speed. Otherwise, encryption overhead may cause a minor slowdown. For detailed tests,
Do I need a VPN on my phone?
Yes — mobile VPNs protect data sent over public Wi-Fi or mobile networks. They encrypt app communications and help avoid tracking. See also.
Can a VPN bypass regional restrictions on streaming sites?
Yes. A VPN can make your connection appear as if it’s from another country, granting access to geo-blocked content. However, some platforms detect and block VPN IP ranges. Learn more in.
Is it legal to use a VPN everywhere?
No. VPN legality varies by country. While VPNs are legal in most regions, some governments (like China or Iran) restrict them to approved providers. For compliance advice, check.
Does a VPN hide browsing from Google or websites?
Partially. A VPN hides your IP and location, but websites can still identify you through cookies, account logins, or browser fingerprints. To reduce tracking, use privacy-focused browsers and clear cookies regularly.
Can I use a VPN for gaming safely?
Yes — VPNs can stabilize ping routes and protect against DDoS attacks in online games. Choose a provider with nearby servers to minimize latency. Learn setup steps in.
Will a VPN work with Ethernet connections?
Absolutely. VPNs encrypt traffic regardless of connection type — Wi-Fi or Ethernet. Configuration depends on your OS and VPN client. See.
Can a VPN bypass IP bans or parental controls?
Usually, yes. By assigning a new IP address, VPNs can circumvent bans or restrictions, but this may violate platform policies.