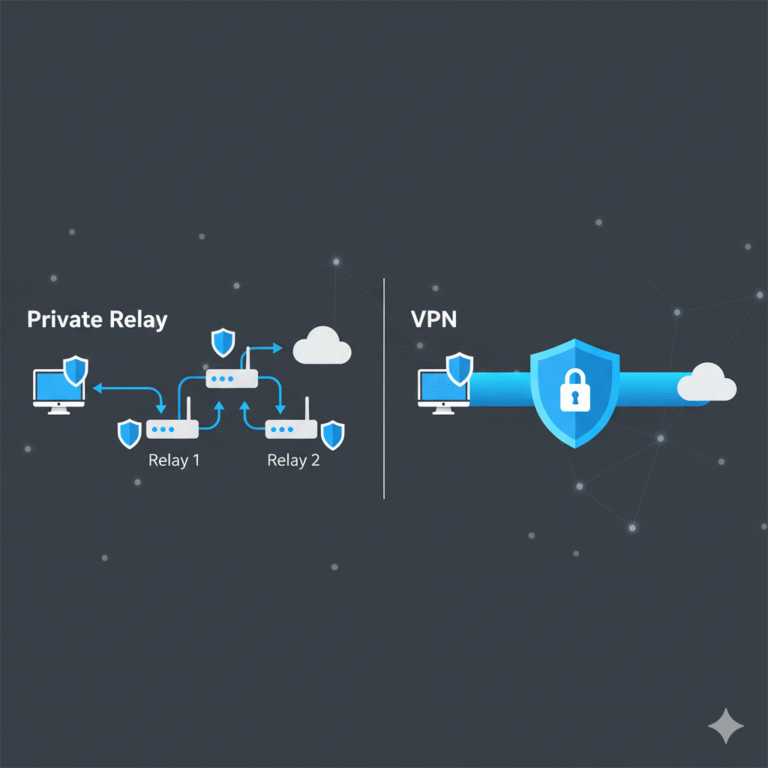
VPN stands for Virtual Private Network — a secure technology that encrypts your internet connection and routes it through a private server. This tunnel hides your IP address, protects your data, and maintains your privacy while online (source: Wikipedia).
For a deeper breakdown of core concepts, you can read What is a VPN: Definition, Benefits & Uses, which explores how VPNs fit into modern digital security frameworks.
Why is knowing “what does vpn stand for” important?
Understanding exactly what VPN stands for goes beyond knowing its acronym. It helps users and network professionals interpret how the technology functions within broader cybersecurity ecosystems.
When you understand the purpose and scope of a Virtual Private Network, you can make smarter choices between different providers — such as comparing AirVPN vs NordVPN for better security and speed — and identify the ideal configuration for your needs.
How does a VPN work at a high level?
A VPN works by creating an encrypted tunnel between your device and a secure remote server. Your internet traffic is routed through this tunnel, masking your identity and location.
Here’s the process:
- The VPN client on your device authenticates with a VPN server.
- Encryption protocols such as OpenVPN, WireGuard, or IPsec create a secure tunnel.
- Your IP address is replaced by that of the VPN server, ensuring anonymity.
- The VPN decrypts traffic at the endpoint before forwarding it to its final destination (source: Cloudflare Learning Center).
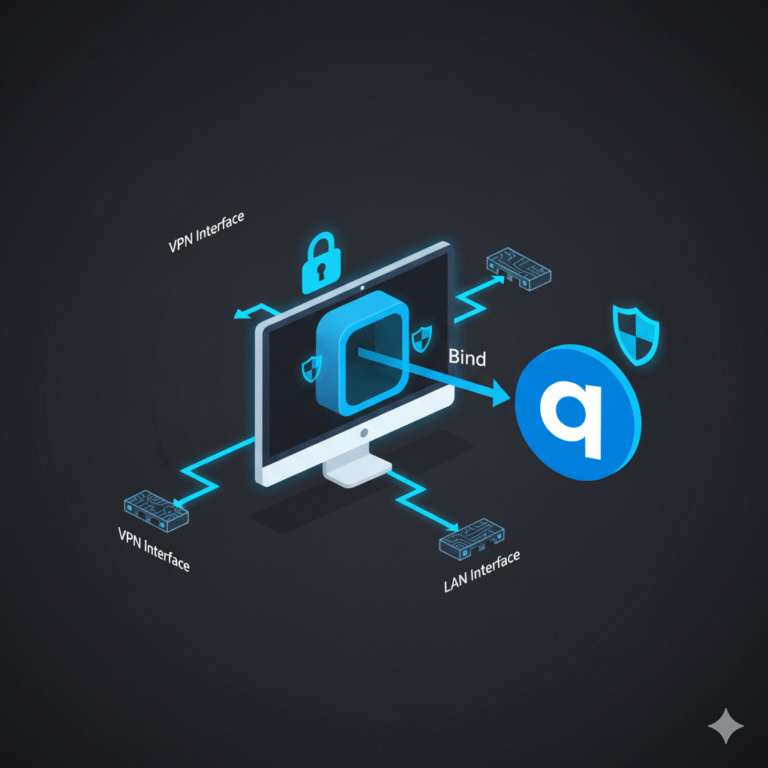
For those interested in device-specific implementations, see how to bind qBittorrent to VPN for secure torrenting or does VPN work with Ethernet — secure wired VPN usage.
What are the main types of VPN?
Not all VPNs are built alike. Depending on your environment, one type may serve better than another.
Remote Access VPN
Used by individual users to connect to corporate networks or remote servers. This type is ideal for remote employees accessing company resources.
Site-to-Site VPN
Connects two networks (e.g., different office locations) securely over the internet. For example, you can explore which statement describes an important characteristic of a site-to-site VPN to understand its architecture.
VPN Concentrator
An enterprise-grade device that manages multiple VPN tunnels simultaneously — covered in detail in what is a VPN concentrator: secure multi-tunnel VPN device.
Mobile VPN
Designed for users who frequently switch between Wi-Fi and cellular networks, ensuring a persistent, stable connection.
Provider-Provisioned VPN (PPVPN)
Offered by ISPs or telecom companies, these solutions emphasize scalability over anonymity (source: TechTarget).
What are the security and privacy benefits of a VPN?
A properly configured VPN provides critical privacy and protection benefits:
- Data encryption: Prevents interception on public Wi-Fi.
- IP masking: Hides your true IP from websites and ISPs.
- Geo-restriction bypass: Lets you access content limited to other regions — for instance, you can watch Jio Cinema in the USA without VPN or explore how to change TikTok region with VPN.
- ISP throttling prevention: Some ISPs slow down specific traffic; VPNs can reduce this discrimination.
- Enhanced security in restricted regions: Essential where internet freedom is limited — see is VPN legal in China – what you must know (2025).
To assess practical VPN performance, refer to independent evaluations like the NordVPN review: Top Features & Performance in 2025 or ExpressVPN Review – Tested in 2025.
What are common limitations and risks of using a VPN?
While VPNs enhance security, they’re not perfect:
- Reduced speed: Routing traffic through an extra server introduces latency.
- Trust in provider: Your privacy depends on the provider’s logging policies. For example, compare privacy promises in the ProtonVPN review 2025 and Surfshark review 2025.
- Incompatibility issues: Some apps block VPN traffic or require manual configuration (see why does weave not work when VPN is on – fix guide).
- Limited endpoint protection: VPNs encrypt your connection but don’t protect against malware or phishing sites.
- Legal constraints: In countries with strict regulations, VPN use may be monitored or restricted.
For users comparing privacy alternatives, Is DNSCrypt an Alternative to VPN? explores technical trade-offs between DNS encryption and full VPN tunneling.
Constraints and performance:
Testing constraints:
Performance tests depend on protocol choice, distance to server, encryption level, and ISP quality. No single benchmark applies universally.
Performance caveats:
Speed reductions of 5-30% are common, especially when connecting to overseas servers. Mobile networks introduce additional variability.
Pragmatic guidance:
- Use newer protocols like WireGuard or OpenVPN 2.6+ for optimal throughput.
- Test several regions — nearby servers often yield the best latency.
- Check for DNS and IPv6 leaks before trusting “100% anonymity” claims.
- Compare multiple providers’ results and log policies using the Private Internet Access (PIA) review 2025 – Is It Worth It?.
How do VPN protocols differ and affect performance?
The protocol defines how a VPN establishes its tunnel and encryption. Different protocols balance speed, security, and compatibility:
OpenVPN — an open-source standard built on SSL/TLS that supports both TCP and UDP modes. It’s widely adopted and offers a strong balance between security and flexibility (source: OpenVPN.net).
WireGuard — a newer, lightweight protocol using state-of-the-art cryptography for faster handshake and minimal codebase. It often delivers better throughput and lower battery consumption.
IKEv2/IPsec — ideal for mobile devices due to its ability to reconnect quickly when switching networks.
L2TP/IPsec and PPTP — legacy options now considered obsolete due to weaker encryption.
To compare real-world results, see performance insights from the ProtonVPN review: Privacy, Speed, Free Plan and the CyberGhost VPN review | Tested in 2025 – Speed & Privacy.
What are practical use cases of a VPN today?
VPNs serve both enterprise and individual needs:
Corporate access and remote work
Companies rely on VPNs to let employees connect securely to internal systems. For multi-office scenarios, a point-to-point VPN (also known as a site-to-site VPN) links separate branches through encrypted tunnels.
Streaming and region-locked services
Users employ VPNs to bypass regional content blocks — e.g., learning how to unblock Roblox at school without VPN or accessing local libraries like BBC iPlayer or Netflix UK from abroad.
Gaming optimization
Some gamers use VPNs to reduce ping or reach exclusive servers. However, results vary — explained in Does Using a VPN Help with Ping?.
Enhanced privacy tools
A VPN complements encrypted DNS or Tor, though they address different layers. If you’re curious about DNS-only encryption, see Is Encrypted DNS an Alternative to VPN.
How secure are free VPNs compared to paid options?
Free VPNs often appear appealing, but most impose limits or privacy compromises. Common issues include:
- Data logging and resale — Many free providers monetize by selling user data (source: CNET).
- Limited bandwidth and server choice — leading to slow speeds and congestion.
- Weaker encryption — some use outdated protocols or skip key verification.
Paid options generally maintain no-logs policies, offer audited infrastructure, and include kill switches and leak protection. Reviews like PureVPN review 2025 – Privacy, Speed & Value and ExpressVPN Review – Speed, Privacy & Ease demonstrate these differences.
What myths or misconceptions surround VPNs?
Myth 1: A VPN makes you completely anonymous.
Reality: It hides your IP but not your identity if you log into personal accounts.
Myth 2: All VPNs are equally secure.
Reality: Security depends on protocol, encryption, and provider trust.
Myth 3: A VPN always improves speed.
Reality: Encryption overhead and longer routing usually reduce raw speed, though sometimes a VPN can bypass ISP throttling.
For guidance on troubleshooting, check Why Does My Google Chrome Never Stay Signed In VPN – Fix It Fast and Why Does Weave Not Work When VPN Is On – Fix Guide.
What is the future of VPN technology?
VPN technology continues to evolve with these trends:
- Quantum-resistant encryption — researchers are testing new algorithms to secure tunnels against future quantum attacks.
- Integrated privacy stacks — VPNs combined with encrypted DNS, firewall rules, and AI-based anomaly detection.
- Protocol convergence — WireGuard integration into mainstream OSs like Android 14 and macOS Sonoma improves efficiency (source: Android Developers).
- Edge computing & decentralized VPNs — emerging peer-to-peer models distribute nodes globally for better resilience.
These innovations suggest that VPNs will remain core tools for privacy-centric networking, especially as regulations tighten around data sovereignty.
Conclusion
Knowing exactly what does VPN stand for empowers users to evaluate providers, understand security limitations, and deploy the right protocol for their needs. Whether you’re streaming abroad, securing a business connection, or minimizing digital tracking, a Virtual Private Network remains one of the most versatile tools for online privacy.
For extended reading, explore What Does a VPN Do — Benefits & How It Works or advanced setups like Can a VPN Bypass an IP Ban?.


人生多艰,快乐一天是一天!