Many people ask, “can vpn be tampered?” The short answer is yes—under certain conditions. VPNs encrypt traffic in transit, but misconfigurations, local-network attacks, and weak providers can still expose or reroute data. Below, we explain how tampering actually happens, then give you a prioritized checklist to prevent it—plus linked resources if you want to dive deeper or troubleshoot edge cases.
Quick Answer: When Tampering Becomes Possible
- On the same local network: A hostile Wi-Fi hotspot or shared LAN can try to reroute some traffic outside the tunnel if your client is laxly configured.
- At the device layer: Malicious or low-quality VPN apps, risky split-tunneling rules, or disabled kill switches create openings.
- Beyond the VPN server: Once traffic exits the VPN server, only end-to-end HTTPS/TLS prevents modification—plain HTTP stays tamperable.
Want a deeper tech primer? See what is a vpn concentrator: Secure Multi-Tunnel VPN Device for enterprise-grade context:
what is a vpn concentrator: Secure Multi-Tunnel VPN Device
How VPNs Are Supposed to Prevent Tampering
- Encryption + integrity: Modern VPNs (e.g., WireGuard, IKEv2/IPsec, TLS-based) use authenticated encryption that blocks undetected packet edits inside the tunnel.
- Trust boundary: The tunnel secures you to the VPN server. After that, end-to-end HTTPS to each site is still essential.
- Full vs. split tunnel: Full-tunnel sends everything through the VPN; split-tunnel can leave some apps exposed to local-network interference if misused.
If you’re comparing providers on security posture, start here:
- AirVPN vs NordVPN: Which VPN Offers Better Security & Speed?
- NordVPN Review: Top Features & Performance in 2025
- ExpressVPN Review – Tested in 2025: Speed, Privacy & Ease
What Actually Gets “Tampered” in Practice (Case-Driven View)
- Routing/decloaking on shared networks: Misconfigurations can let some traffic escape the tunnel to the local LAN/ISP.
- DNS & plaintext protocols: If you use plain HTTP (or legacy protocols), an on-path attacker can read/modify it even while the VPN is on.
- Unvetted apps & free VPNs: Some mobile VPNs request invasive permissions or leak traffic; always choose reputable, audited services. See reviews:
- Surfshark review 2025 – Fast, Secure & Unlimited Devices?
- ProtonVPN review: Tested in 2025 – Privacy, Speed, Free Plan
- Private Internet Access (PIA) review 2025 – Is It Worth It?
- PureVPN review: Tested in 2025 – Privacy, Speed & Value
- CyberGhost VPN review | Tested in 2025 – Speed & Privacy
- IPVanish review: Speed, Privacy & Threat Protection Tested in 2025
Hardening Checklist: The Highest-Impact Fixes First
- Go full-tunnel by default. Disable split tunneling unless you really need it.
- Enable the kill switch and (if available) “Block LAN while connected.”
- Force HTTPS everywhere. Turn on your browser’s HTTPS-Only mode; avoid plaintext protocols.
- Keep the client and OS updated (auto-update ON).
- Use provider DNS inside the tunnel or encrypted DNS that respects your policy.
- Lock down your LAN/Wi-Fi: Strong WPA2/3, unique passwords, and disable insecure guest bridging.
- Prefer modern protocols (WireGuard or IKEv2/IPsec with strong ciphers).
- Audit your apps: Remove shady “free VPNs,” browser extensions, and unneeded split-tunnel rules.
- Verify for leaks after major changes. For P2P users:
Troubleshooting edge cases:
- Chrome sign-in issues with VPN? → why does my google chrome never stay signed in vpn – Fix It Fast
- App conflicts (e.g., Weave) → Why Does Weave Not Work When VPN Is On – Fix Guide
Step-By-Step: Configure a Safer Setup (Home or Coffee-Shop Wi-Fi)
- Install a reputable client and sign in.
- Choose a modern protocol (WireGuard/IKEv2).
- Set “Full-Tunnel,” disable split-tunneling unless required.
- Toggle “Kill Switch” + “Block LAN.”
- Enable HTTPS-Only in the browser; avoid HTTP sites.
- Reconnect and run a leak test; re-test any apps that must bypass the tunnel.
- Harden the router: unique admin password, auto-updates; if available, enable DHCP/ARP protections.
- Re-evaluate locations for speed/latency (see gaming tips below).
Gaming & latency guides:
Myths vs Reality
- Myth: “A VPN makes me untraceable.”
Reality: Trackers still work via cookies, account logins, and browser fingerprinting. - Myth: “VPNs stop all hacks.”
Reality: Device-level malware/phishing is out of scope—use endpoint protection. - Myth: “Any VPN is fine.”
Reality: Provider quality, audits, and jurisdiction matter—see reviews linked above.
Practical Scenarios & Related Guides
Streaming & region access
- Geo content tips (without a VPN):
- TikTok region:
Gambling & policy compliance
- Can I Use a VPN for FanDuel – Legal Access Guide
- Can You Use FanDuel With a VPN? What to Know in 2025
Legal & regulatory
Privacy tech alternatives / complements
Torrents & downloads
- Do I Need VPN for Direct Download? Find Out Now
- Which Is Better uTorrent or qBittorrent a VPN
- can i use stremio without vpn – Risks & Safe Streaming
Remote access & enterprise
- is logmein a vpn? Secure Hamachi Remote Access
- a point to point vpn is also known as a site-to-site VPN
- which statement describes an important characteristic of a site-to-site vpn
App-specific “how-tos” & fixes
- How to Turn Off VPN Mac in Seconds | Quick Guide
- how to download capcut with vpn – Step-by-Step Guide
- why is my vpn establishment from a remote user disabled
- Does reCAPTCHA Work on VPN – Full Guide
Niche & community
- do you need to use a vpn for leaked.cx – Speed & Access Tips
- does koa allow vpn access – Secure Your Camping Wi-Fi
- What Location to Put VPN for Unrestricted Chat GPT
- can i run a vpn with hughesnet – Speed & Compatibility Guide
- how does a vpn block roku from your privacy | Protect Roku Streaming
Security & access control
Pros & Cons (Balanced View)
Pros
- Encrypts traffic and adds integrity checks against undetected modification within the tunnel.
- Masks your IP/location from destination services and local networks.
- Centralizes DNS/security policies when correctly configured.
Cons
- Routing or client misconfigurations can leak traffic around the tunnel.
- Weak or shady providers (especially “free” apps) may log or mishandle data.
- Doesn’t stop phishing/malware or cookie-based tracking by itself.
Frequently Asked Questions
1) Can a VPN be “tampered with” by attackers?
Yes, in specific conditions. The most realistic threats are on shared Wi-Fi/LANs where attackers try to route some traffic outside the tunnel or target plaintext protocols. Full-tunnel, kill switch, and HTTPS-only browsing reduce this risk drastically.
2) Does a VPN stop man-in-the-middle attacks completely?
Inside the tunnel, integrity checks make undetected edits impractical. Beyond the VPN server, you still rely on HTTPS/TLS to each site. Avoid HTTP and legacy protocols; turn on your browser’s HTTPS-Only mode.
3) Can governments or ISPs tamper with VPN traffic?
They typically prefer to block or throttle VPNs rather than decrypt them. Some networks use traffic shaping or DPI to disrupt connections. Obfuscation modes and modern protocols help you stay connected where lawful.
4) Is split tunneling safe?
Use sparingly. Apps that bypass the tunnel can be exposed to local-network tampering. If you must split, restrict it to a minimal allow-list and keep the kill switch enabled.
5) If my VPN drops for a second, can data be altered?
If the kill switch is off, apps may momentarily send plaintext or direct traffic. With the kill switch on, traffic blocks during drops, preventing accidental exposure.
6) Are free VPNs safe to use?
Sometimes, but many are risky: invasive permissions, opaque logging, or weak encryption. Prefer audited, well-reviewed services (ProtonVPN review, Surfshark review 2025, etc.).
7) Which protocol is most resilient right now?
WireGuard and IKEv2/IPsec are excellent modern choices. What matters just as much is how you configure your client (full-tunnel, kill switch) and your LAN (secure Wi-Fi, router hygiene).
8) Does a VPN improve gaming ping?
Sometimes—if it gives you a shorter route. But it can also add overhead. See: Does Using a VPN Help with Ping? Find Out Now.
9) Can a VPN bypass every site restriction or ban?
No. Some services use device/browser signals, phone verification, or account histories. Read: Can a VPN Bypass an IP Ban? Find Out Now.
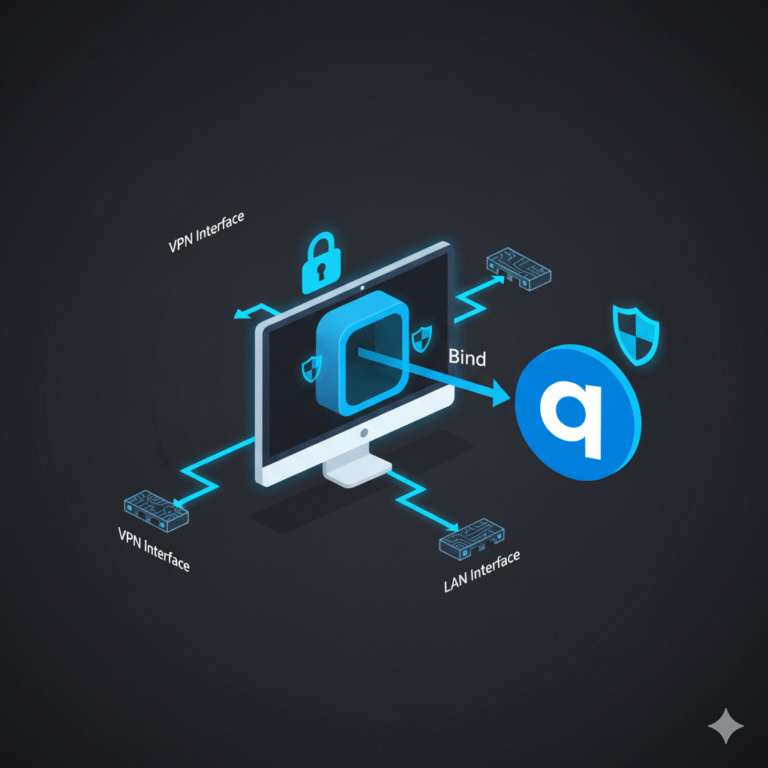
10) How do I safely torrent behind a VPN?
Bind your client to the VPN interface, test for leaks, and keep the kill switch on:
how to bind qbittorrent to vpn for secure torrenting.
11) What if I just need to turn the VPN off quickly on Mac?
Follow this quick guide: How to Turn Off VPN Mac in Seconds | Quick Guide.
12) Is there a simpler alternative to a VPN for privacy?
Encrypted DNS (e.g., DNS over HTTPS) helps with DNS privacy but doesn’t replace a VPN’s tunnel. See:
Is DNSCrypt an Alternative to VPN? Explained Simply and
Is Encrypted DNS an Alternative to VPN.
Comparison Table (for your designer/writer)
| Attack/Issue | What’s At Risk | Attacker Position | Core Cause | Primary Mitigations |
|---|---|---|---|---|
| Routing leak / decloaking | Some traffic outside tunnel | Same LAN / Hotspot | Lax client routes / split-tunnel | Full-tunnel, kill switch, LAN block, router hygiene |
| Plain HTTP over VPN | Read/modify app data | Any on-path | No end-to-end crypto | HTTPS-Only mode; avoid legacy plaintext protocols |
| Shady/free VPN apps | Privacy, metadata, stability | App/vendor | Weak encryption/logging | Audited providers; review independent tests |
| Mis-set DNS outside tunnel | DNS hijack/visibility | Local ISP / LAN | Wrong resolver / policy | Use VPN-provided/encrypted DNS inside tunnel |
Conclusion
A well-configured VPN is extremely hard to “tamper with” in a way that silently alters your traffic. Most real-world problems come from misconfiguration, plaintext protocols, or weak providers. If you lock down full-tunnel + kill switch, force HTTPS, secure your Wi-Fi/router, and choose a vetted service, you’ll remove the biggest risks—and enjoy the speed/privacy benefits VPNs were built for.
If you’re choosing a provider or comparing security features, these deep dives help: